UA
6 Min Read
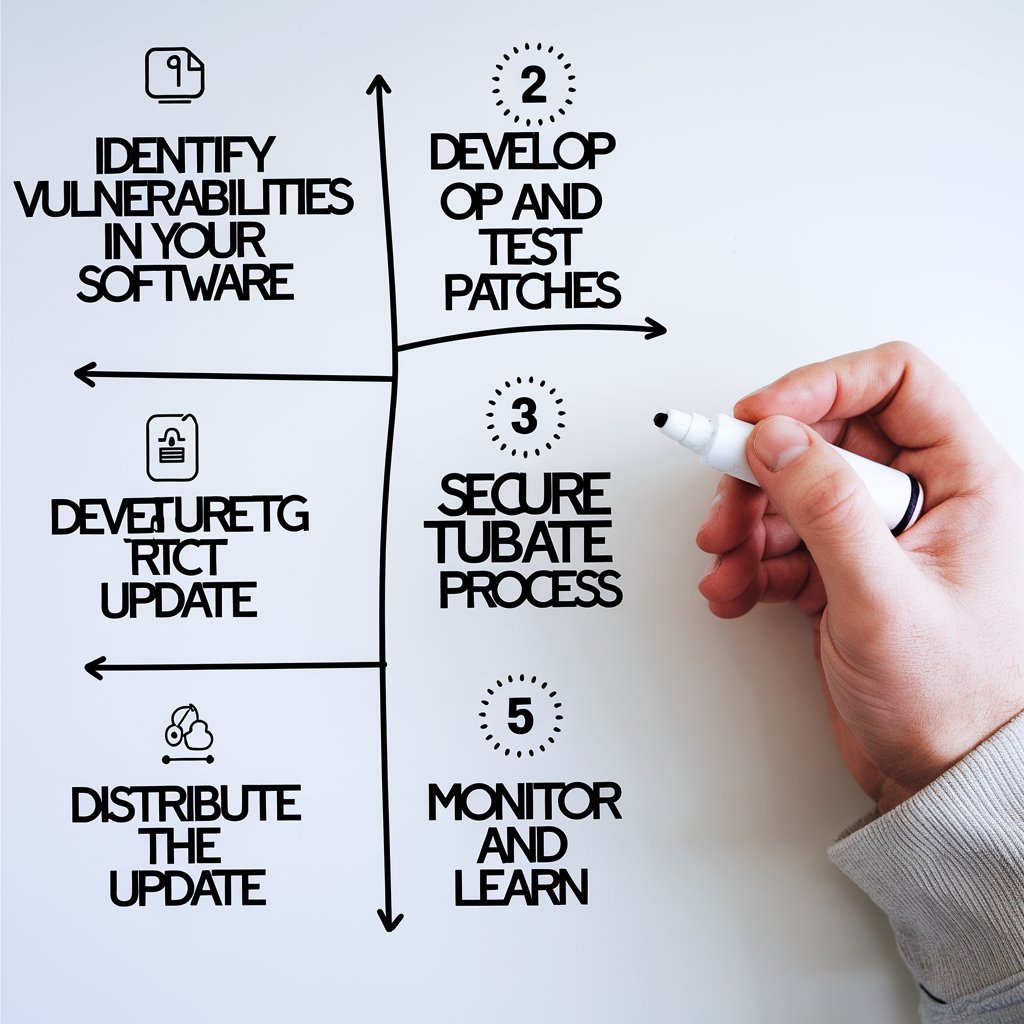
Why Secure Software Updates Matter
Software updates are released for various reasons:
Patching Security Vulnerabilities: Updates often contain critical fixes for security flaws that attackers can exploit.
Bug Fixes: Updates address bugs and errors in software, improving stability and performance.
New Features: Updates may include new features, functionality, or enhancements.
Performance Improvements: Updates often optimize software to improve performance and speed.
Compliance Requirements: Some regulatory standards require software to be kept up-to-date with the latest security patches.
If you fail to apply security updates promptly, you expose your systems and data to known vulnerabilities. Furthermore, if updates are not properly vetted, they could introduce security risks instead of mitigating them.
Key Challenges in Implementing Secure Software Updates
Complexity: Managing updates across diverse systems and applications can be complex.
Downtime: Applying updates can sometimes require system downtime, which can be disruptive.
Compatibility Issues: Some updates may cause compatibility issues with other software.
Security Risks: If update processes are compromised, malicious code could be injected into your systems.
Testing Requirements: Thoroughly testing updates before deployment is crucial, but can be time-consuming.
Patch Fatigue: The sheer volume of updates can lead to patch fatigue and increase the risk of overlooked updates.
Best Practices for Implementing Secure Software Updates
Here are practical steps for implementing a secure software update process:
Create an Update Policy:
What it is: A document outlining your organization's approach to software updates.
How it helps: Provides a framework for consistent and timely updates.
Best Practices:
Define the frequency of updates.
Establish clear roles and responsibilities for update management.
Outline procedures for testing, deploying, and tracking updates.
Define communication strategies to keep stakeholders informed.
Automate Updates Where Possible:
What it is: Use automated tools to streamline the update process.
How it helps: Reduces the risk of human error, speeds up the update process, and ensures consistent patching.
Best Practices:
Use patch management systems to automate update deployment.
Configure tools to automatically download and install updates.
Set up alerts to notify administrators of failed or problematic updates.
Key Tools: Microsoft SCCM, Patch Manager Plus, Ansible, Chef.
Prioritize Updates:
What it is: Focus on applying critical security patches first, based on risk assessments.
How it helps: Mitigates the most significant risks quickly and efficiently.
Best Practices:
Use vulnerability scanners to identify critical vulnerabilities.
Prioritize updates based on severity and exploitability.
Apply security updates promptly, especially those that address known vulnerabilities.
Key Tools: Vulnerability scanners like Nessus, OpenVAS, and Qualys.
Establish a Testing Environment:
What it is: Test updates in a non-production environment before rolling them out to production systems.
How it helps: Identifies compatibility issues, performance problems, and other unforeseen issues before they can affect your live systems.
Best Practices:
Use a test environment that closely mirrors your production environment.
Test updates thoroughly, including regression testing.
Involve end-users in user acceptance testing (UAT).
Implement a Rollback Plan:
What it is: Have a plan to quickly roll back updates if problems occur.
How it helps: Minimizes downtime and disruption caused by problematic updates.
Best Practices:
Maintain backups of your systems and data.
Test your rollback plan regularly.
Ensure that administrators know how to revert to previous versions.
Verify Update Authenticity:
What it is: Ensure that updates are from trusted sources and have not been tampered with.
How it helps: Prevents the installation of malware or compromised updates.
Best Practices:
Download updates from the vendor’s official website or trusted repositories.
Verify the digital signatures of updates to ensure integrity.
Use trusted channels for receiving updates and notifications.
Segment Your Network:
What it is: Divide your network into smaller segments and control access between them.
How it helps: Limits the spread of malware if an update process is compromised.
Best Practices:
Isolate production networks from testing environments.
Implement firewall rules to control traffic between different network segments.
Use a zero-trust approach to limit access to sensitive data.
Monitor Updates:
What it is: Track the status of updates across your organization.
How it helps: Identifies systems that haven’t been updated and allows for quick remediation.
Best Practices:
Use reporting features in patch management systems.
Generate regular reports on update status.
Use dashboards to visualize update progress.
Train Employees:
What it is: Educate employees about the importance of software updates.
How it helps: Improves awareness and reduces the risk of users delaying or ignoring updates.
Best Practices:
Include update awareness training in security training programs.
Explain the risks of not applying updates.
Provide instructions for installing updates when required.
Use a Centralized Patch Management System:
What it is: A centralized platform for managing software updates across all systems in your organization.
How it helps: Streamlines the update process, provides better visibility, and enables more effective control over patching.
Best Practices: Implement a reputable patch management solution and integrate it with other security tools.
Tools for Secure Software Updates
Patch Management Software: Microsoft SCCM, Patch Manager Plus, Automox, ManageEngine Patch Manager
Vulnerability Scanners: Nessus, OpenVAS, Qualys, Rapid7
Configuration Management Tools: Ansible, Puppet, Chef
Endpoint Detection and Response (EDR) Solutions: CrowdStrike, SentinelOne, Microsoft Defender for Endpoint
Conclusion
Implementing secure software updates is a critical task for any organization that seeks to protect its data and systems. By adopting these best practices, you can reduce the risks associated with vulnerabilities and ensure a more secure environment. Remember, it's not just about applying updates; it’s about having a well-defined, tested, and automated process in place. audit3aa
Join our newsletter list
Sign up to get the most recent blog articles in your email every week.
You can copy our materials only after making sure that your services are safe.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.