UA
10 Min Read
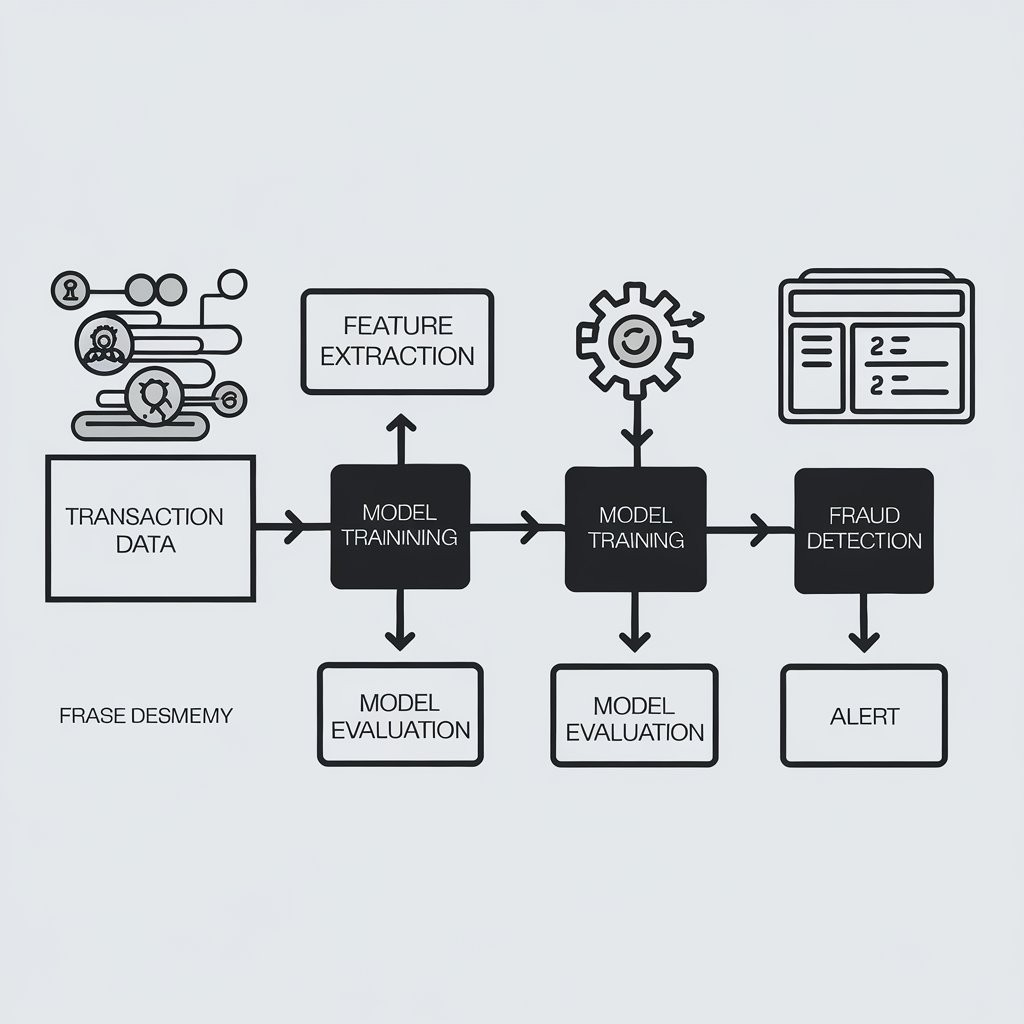
1. What Are Fraud Detection Algorithms?
Fraud detection algorithms are advanced software tools powered by machine learning, artificial intelligence, and statistical methods that are designed to identify suspicious activities, patterns, or transactions indicative of fraud. These algorithms analyze data from various sources—such as transaction history, user behavior, device information, and more—to detect anomalies and prevent fraudulent activities before they occur.
Unlike traditional fraud detection methods, which often rely on predefined rules and patterns, modern algorithms continuously learn from new data and adapt to emerging threats. This makes them highly effective in combating fraud, especially in real-time transactions.
2. The Role of Machine Learning in Fraud Detection
Machine learning is one of the key drivers behind the success of modern fraud detection algorithms. Here's how ML is transforming fraud detection:
a) Continuous Learning and Adaptation
Machine learning algorithms are capable of learning from historical data and adjusting their predictions based on new trends and patterns. This dynamic learning allows them to detect previously unknown fraud schemes or adapt to evolving fraudulent tactics, making them more effective than static rule-based systems.
b) Anomaly Detection
ML algorithms excel at identifying anomalies in vast datasets. In the context of fraud detection, they can spot transactions that deviate from a user’s typical behavior (e.g., an unusually large transfer or spending spree) and flag them for further review. This real-time anomaly detection can help prevent fraudulent activities before they escalate.
c) Predictive Modeling
Machine learning models use historical data to predict the likelihood of fraud. By analyzing thousands of variables (transaction amount, user history, geographical location, etc.), these models can assign a risk score to each transaction and flag high-risk activities for investigation.
3. Real-Time Fraud Prevention
One of the biggest advancements in fraud detection algorithms is their ability to operate in real-time. In the past, fraud detection often involved delays in identifying fraudulent transactions, which allowed fraudsters to take advantage of the time lag. With real-time fraud detection, transactions can be analyzed instantly as they occur, and suspicious activity can be flagged immediately.
This is especially important in industries like banking and e-commerce, where fraud prevention is critical for protecting customer accounts and financial data. For example, if a user attempts to make a large purchase from an unfamiliar location or device, the fraud detection algorithm can immediately alert the system and block the transaction or require additional verification (e.g., multi-factor authentication).
4. Behavioral Analytics for Fraud Detection
Behavioral analytics is a powerful technique used in fraud detection algorithms to identify deviations in user behavior. By establishing a baseline of normal behavior for each user (e.g., typical spending habits, frequent locations, transaction frequencies), algorithms can detect when a user’s actions appear unusual or suspicious.
For example, if a customer who usually makes small purchases suddenly attempts a large withdrawal from an international ATM, the system would flag this as abnormal behavior. The algorithm can analyze multiple data points, including:
Login patterns
Device usage
Geolocation
Transaction types and amounts
Behavioral analytics can also detect patterns of account takeover or synthetic identity fraud, where a fraudster assumes another person’s identity.
5. Fraud Detection in Different Industries
Fraud detection algorithms are not limited to financial institutions. They have become essential in many industries, each facing unique fraud risks.
a) Banking and Payments
In banking and financial services, fraud detection algorithms are used to monitor transactions in real-time and prevent activities such as:
Credit card fraud
Account takeovers
Money laundering
By analyzing transaction data, algorithms can detect suspicious activities, such as abnormal account activity or irregular transfers, and instantly take action to prevent financial losses.
b) E-Commerce
E-commerce platforms are also benefiting from fraud detection algorithms. Algorithms monitor online transactions to detect fraudulent purchases, payment reversals, or fake reviews. They analyze customer information, payment methods, shipping addresses, and even browsing behavior to prevent fraud.
c) Insurance
Insurance companies use fraud detection algorithms to identify suspicious claims. These algorithms analyze claim patterns, medical records, and historical data to uncover fraudulent behavior, such as exaggerated claims or falsified documents.
d) Healthcare
Fraud detection in healthcare involves identifying fraudulent claims, billing inconsistencies, and provider fraud. Machine learning algorithms can analyze patient data, prescriptions, and billing history to spot fraud in real-time.
6. Benefits of Fraud Detection Algorithms
Fraud detection algorithms offer numerous benefits to organizations across various industries:
Increased Accuracy: Algorithms can detect fraud with higher accuracy than manual reviews or rule-based systems. Machine learning models are continuously updated to reflect new fraud trends.
Cost Efficiency: By automating fraud detection, businesses can reduce the need for manual monitoring and investigation, saving valuable time and resources.
Real-Time Protection: With real-time monitoring, fraudsters can be caught in the act, preventing financial losses and minimizing damage.
Adaptability: Fraud detection algorithms can be fine-tuned to adapt to changing fraud tactics, keeping pace with sophisticated fraud schemes.
Enhanced Customer Experience: By preventing fraud without disrupting legitimate transactions, algorithms provide a seamless user experience while ensuring security.
7. The Future of Fraud Detection Algorithms
The future of fraud detection algorithms is promising, with ongoing advancements in AI and machine learning driving innovation. Some trends to watch for include:
AI-Powered Fraud Prevention: As AI technologies become more advanced, fraud detection algorithms will become even more accurate in predicting and preventing fraudulent activities.
Cross-Platform Fraud Detection: With the rise of multi-channel transactions (e.g., mobile apps, websites, in-store purchases), future algorithms will be able to detect fraud across different platforms and devices.
Collaborative Fraud Detection: Organizations may share anonymized data with others to improve fraud detection capabilities across industries, creating a collective defense against fraud.
Conclusion
Fraud detection algorithms are fundamentally changing how businesses and financial institutions protect themselves from fraud. With the power of machine learning, behavioral analytics, and real-time monitoring, these algorithms are providing smarter, faster, and more efficient ways to identify and prevent fraud. As technology continues to evolve, we can expect even greater advancements in fraud detection, offering enhanced security and a safer digital experience for consumers and businesses alike. audit3aa
Join our newsletter list
Sign up to get the most recent blog articles in your email every week.
Similar Topic
Related Blogs
More Articles
Latest Blogs
Frequently Asked Questions
Wondering About Something? Let’s Clear Things Up!
We’ve gathered all the important info right here. Explore our FAQs and find the answers you need.
What types of cybersecurity services does Audit3A offer?
Audit3A provides comprehensive cybersecurity services including application and infrastructure security, cybersecurity governance risk and compliance, SIEM solutions, vulnerability management, and anti-malware solutions. We also offer penetration testing, web and mobile application security, and fraud risk management.
How can Audit3A help my business comply with industry-specific regulations?
Our team specializes in assisting organizations with establishing effective cybersecurity governance frameworks, managing cybersecurity risks, and conducting audits for compliance with various regulations and standards. We ensure your cybersecurity practices align with industry best practices and regulatory requirements specific to your sector.
What makes Audit3A different from other cybersecurity companies?
Audit3A stands out due to our comprehensive approach, combining advanced technology with expert human analysis. We offer tailored solutions for businesses of all sizes, have a global presence with local expertise, and maintain a strong focus on research and development to stay ahead of emerging threats.
How often should my organization conduct a cybersecurity audit?
The frequency of cybersecurity audits can vary depending on your industry, regulatory requirements, and risk profile. However, we generally recommend conducting a comprehensive audit at least annually, with more frequent assessments of specific areas or in response to significant changes in your IT environment.
Can Audit3A provide cybersecurity solutions for small businesses as well as large enterprises?
Yes, Audit3A offers scalable solutions suitable for organizations of all sizes. We have specific packages designed for small businesses that provide essential security measures while being cost-effective. Our team can tailor our services to meet the unique needs and budget constraints of your business.
What is the process for engaging Audit3A's services?
The engagement process typically begins with an initial consultation to understand your specific needs and challenges. We then conduct a preliminary assessment of your current security posture. Based on this, we propose a customized security plan. Once agreed, we implement the solutions, provide necessary training, and offer ongoing support and monitoring.
How does Audit3A stay updated with the latest cybersecurity threats and technologies?
Audit3A invests heavily in research and development. We have our own R&D lab dedicated to studying emerging cyber threats. We also collaborate with leading universities, participate in developing international security standards, and maintain a program for independent security researchers. Our team regularly updates their skills and certifications to stay at the forefront of cybersecurity technology and practices.
You can copy our materials only after making sure that your services are safe.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.









